In the end, the very best prevention for a DDoS assault is an extensive Option that addresses all three varieties of assaults. Verify Stage’s Quantum DDoS safety Option helps prevent Every type, with an extensive suite of instruments and protection techniques.
The steps outlined higher than can only be accomplished by way of a mix of providers, units and persons Performing collectively. For example, to mitigate Layer seven DDoS attacks it is usually needed to do the subsequent:
DDoS assaults and traits How DDoS assaults do the job Throughout a DDoS assault, a number of bots, or botnet, floods a web site or support with HTTP requests and visitors.
If businesses want to attenuate their chance of assaults, they need to carry out up-to-date security answers that account for the steps involved in a successful DDoS attack.
RTX 5050 rumors depth comprehensive spec of desktop graphics card, suggesting Nvidia may well use slower online video RAM – but I wouldn’t panic nonetheless
Being an IT pro, you normally takes steps to help All set yourself for any DDoS assault. Check out the subsequent techniques and applications which can help you productively manage an incident.
As an example, militaries have been recognized to combine DDoS attacks with Actual physical types. Tactical attacks are used to divert awareness from typical IT duties to reap the benefits of a different target – the old bait-and-change cyberattack.
$140 /mo Ideal Resolution to shield your website/server hosted in A further locale from DDoS assaults.
When working with a DDoS attack, there are actually certain very best techniques which can help hold a problem less than control. Notice these DDoS assault do’s and don’ts.
Subsequently, attackers can produce bigger volumes of site visitors in an incredibly shorter timeframe. A burst DDoS assault is often beneficial for your attacker mainly because it is harder to trace.
A DDoS planning scheme will often identify the danger associated when specific methods come to be compromised.
Like legitimate devices administrators, attackers now have voice recognition, device Discovering plus a electronic roadmap that can let them to control built-in devices in your home or Business office, for instance smart thermostats, appliances and residential safety techniques.
To be a mitigation strategy, use an Anycast network to scatter the assault website traffic across a community of distributed servers. This really is executed so which the targeted visitors is absorbed because of the network and turns into extra workable.
DDoS is larger in scale. It utilizes thousands (even thousands and thousands) of related gadgets to satisfy its aim. The sheer quantity in the gadgets utilised will make web ddos DDoS A great deal more difficult to struggle.
 Rider Strong Then & Now!
Rider Strong Then & Now! Ben Savage Then & Now!
Ben Savage Then & Now! Brandy Then & Now!
Brandy Then & Now! Sydney Simpson Then & Now!
Sydney Simpson Then & Now!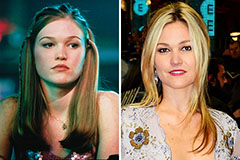 Julia Stiles Then & Now!
Julia Stiles Then & Now!